Enable AKS Azure Active Directory integration with a Managed Identity from an ARM template
When you’re deploying an Azure Kubernetes Service (AKS) cluster in Azure, it is common that you’ll want to integrate it into Azure Active Directory (AAD) to use it as an authentication provider.
The original (legacy) method for enabling this was to manually create a Service Principal and use that to grant your AKS cluster access to AAD. The problem with this approach was that you would need to manage this manually and as well as rolling worry about rolling secrets.
More recently an improved method of integrating your AKS cluster into AAD was announced: AKS-managed Azure Active Directory integration. This method allows your AKS cluster resource provider to take over the task of integrating to AAD for you. This simplifies things significantly.
You can easily do this integration by running PowerShell or Bash scripts, but if you’d prefer to use an ARM template, here is what you need to know.
You will need to have an
object idof an Azure Active Directory group to use as your Cluster Admins.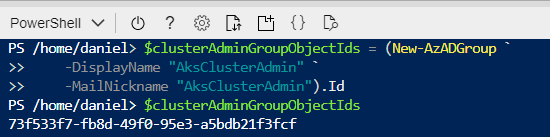
This will return the object Id for the newly create group in the variable
$clusterAdminGroupObjectIds. You will need to pass this variable into your ARM template.You need to add an
aadProfileblock into thepropertiesof your AKS cluster deployment definition: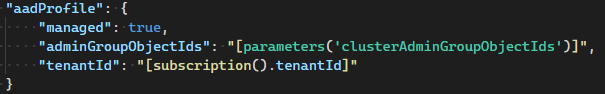 For example:
For example:
When you deploy the ARM template (using whatever method you choose), you’ll need to pass the
$clusterAdminGroupObjectIdsas a parameter. For example:
That is all you really need to get AKS-managed AAD integration going with your AKS cluster.
For a fully formed ARM template for that will deploy an AKS cluster with AKS-managed AAD integration plus a whole lot more, check out this ARM template. It will deploy an AKS cluster including the following:
- A Log Analytics workspace integrated into the cluster with Cluster Insights and Diagnostics.
- A VNET for the cluster nodes.
- An ACR integrated into the VNET with Private Link and Diagnostics into the Log Analytics Workspace.
- Multiple node pools spanning availability zones:
- A system node pool including automatic node scaler.
- A Linux user node pool including automatic node scaler.
- A Windows node pool including automatic node scaler and taints.
Thanks for reading.
